How to Create an Isolated Subnet in AWS: A Comprehensive Guide
Creating an isolated subnet in AWS is crucial for enhancing security and controlling access to your resources. This guide provides a step-by-step walkthrough, covering key concepts and best practices. We'll focus on achieving true isolation, minimizing exposure, and maximizing your cloud security posture.
Understanding AWS Subnets and Isolation
Before diving into the process, let's clarify what we mean by an "isolated subnet." In AWS, a subnet is a range of IP addresses within a Virtual Private Cloud (VPC). An isolated subnet is one that's designed with minimal external access, limiting potential attack vectors. This typically involves:
- No public IP addresses: Instances launched within the isolated subnet won't have public IPs, making them unreachable from the internet.
- Restricted inbound/outbound traffic: Only necessary traffic is allowed in and out, usually via carefully configured security groups and Network Access Control Lists (NACLs).
- Private IP addressing only: Communication within the VPC relies on private IP addresses, further enhancing security.
Step-by-Step Guide to Creating an Isolated Subnet
Here's how to create an isolated subnet within your AWS environment:
1. Existing VPC or New VPC?
First, determine if you need to create a new VPC or use an existing one. For maximum isolation, creating a new VPC dedicated to your isolated resources is recommended.
2. Create a New VPC (If Necessary)
If you're creating a new VPC, use the AWS Management Console, AWS CLI, or CloudFormation. Choose a suitable CIDR block (ensure it doesn't overlap with other VPCs) and define the number of Availability Zones you need.
3. Create the Isolated Subnet
- Choose Availability Zone(s): Select at least one Availability Zone (for high availability). Multiple AZs provide redundancy.
- CIDR Block: Assign a private CIDR block that doesn't overlap with your other subnets or VPC's CIDR. Use a subnet mask appropriate for your network needs (e.g., /24, /26, /28).
- Name Tag: Use a descriptive name (e.g., "Isolated-Subnet-Prod"). Tagging improves organization and management.
4. Configure Security Groups
Security groups act as virtual firewalls, controlling inbound and outbound traffic for instances within the subnet. For an isolated subnet:
- Restrict Inbound Traffic: Only allow necessary inbound traffic, such as SSH (if needed for management), or traffic from other private resources within your VPC.
- Restrict Outbound Traffic: You might need to allow outbound traffic to specific services (e.g., specific AWS services), but generally, keep outbound traffic as restricted as possible.
Strong Recommendation: Use principle of least privilege - only allow absolutely necessary traffic.
5. Configure Network Access Control Lists (NACLs)
NACLs provide an additional layer of security. They filter traffic at the subnet level. While security groups are instance-based, NACLs operate at the subnet level, offering broader control. For an isolated subnet:
- Restrict Inbound Traffic: Mirror the restrictions you implemented in your security group. NACLs should be more restrictive than security groups.
- Restrict Outbound Traffic: Similar to security groups, limit outbound traffic to only essential services.
6. Launch Instances within the Isolated Subnet
Launch EC2 instances within your newly created isolated subnet. Ensure they are associated with the appropriately configured security group. These instances will not have public IPs unless explicitly configured with Elastic IP addresses (generally avoided for isolated environments).
7. Accessing your Isolated Resources
Access to your isolated instances will usually be via other means, such as:
- VPN: Establish a secure VPN connection to your VPC.
- Bastion Host: Use a dedicated bastion host within the VPC (but in a different subnet) to access your isolated resources. This bastion host would have a carefully controlled security group.
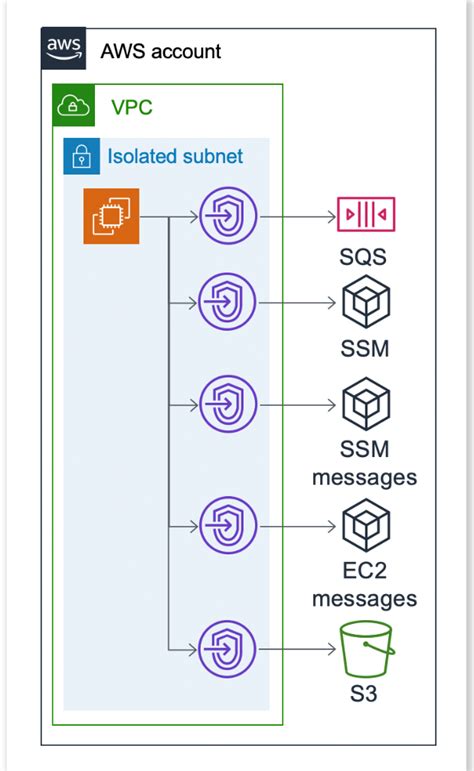
- AWS Systems Manager (SSM): Leverage SSM for remote management, avoiding the need for direct SSH access.
Best Practices for Maximum Isolation
- Regular Security Audits: Regularly review your security groups and NACLs to ensure they align with your security policies.
- Least Privilege: Follow the principle of least privilege when configuring security rules.
- Monitoring: Use CloudWatch to monitor network traffic and identify potential security issues.
- Regular Patching: Keep your instances and AWS services updated with the latest security patches.
By following these steps and best practices, you can effectively create an isolated subnet in AWS, substantially enhancing the security of your cloud resources. Remember, security is an ongoing process, requiring consistent monitoring and adaptation.